Tips on how to confirm the authenticity and origin of photographs and movies – Cyber Tech
Over the previous 18 months or so, we appear to have misplaced the flexibility to belief our eyes. Photoshop fakes are nothing new, after all, however the introduction of generative synthetic intelligence (AI) has taken fakery to an entire new degree. Maybe the primary viral AI faux was the 2023 picture of the Pope in a white designer puffer jacket, however since then the variety of high-quality eye deceivers has skyrocketed into the numerous hundreds. And as AI develops additional, we are able to anticipate an increasing number of convincing faux movies within the very close to future.
One of many first deepfakes to go viral worldwide: the Pope sporting a stylish white puffer jacket
This may solely exacerbate the already knotty drawback of faux information and accompanying pictures. These may present a photograph from one occasion and declare it’s from one other, put individuals who’ve by no means met in the identical image, and so forth.
Picture and video spoofing has a direct bearing on cybersecurity. Scammers have been utilizing faux pictures and movies to trick victims into parting with their money for years. They may ship you an image of a tragic pet they declare wants assist, a picture of a star selling some shady schemes, or perhaps a image of a bank card they are saying belongs to somebody you realize. Fraudsters additionally use AI-generated pictures for profiles for catfishing on courting websites and social media.
Probably the most subtle scams make use of deepfake video and audio of the sufferer’s boss or a relative to get them to do the scammers’ bidding. Only in the near past, an worker of a monetary establishment was duped into transferring $25 million to cybercrooks! That they had arrange a video name with the “CFO” and “colleagues” of the sufferer — all deepfakes.
So what could be accomplished to cope with deepfakes or simply plain fakes? How can they be detected? That is an especially advanced drawback, however one that may be mitigated step-by-step — by tracing the provenance of the picture.
Wait… haven’t I seen that earlier than?
As talked about above, there are completely different sorts of “fakeness”. Generally the picture itself isn’t faux, nevertheless it’s utilized in a deceptive method. Perhaps an actual picture from a warzone is handed off as being from one other battle, or a scene from a film is introduced as documentary footage. In these instances, in search of anomalies within the picture itself received’t assist a lot, however you may attempt looking for copies of the image on-line. Fortunately, we’ve received instruments like Google Reverse Picture Search and TinEye, which may help us do exactly that.
If you happen to’ve any doubts about a picture, simply add it to certainly one of these instruments and see what comes up. You may discover that the identical image of a household made homeless by fireplace, or a gaggle of shelter canines, or victims of another tragedy has been making the rounds on-line for years. By the way, in terms of false fundraising, there are a number of different pink flags to be careful for in addition to the photographs themselves.
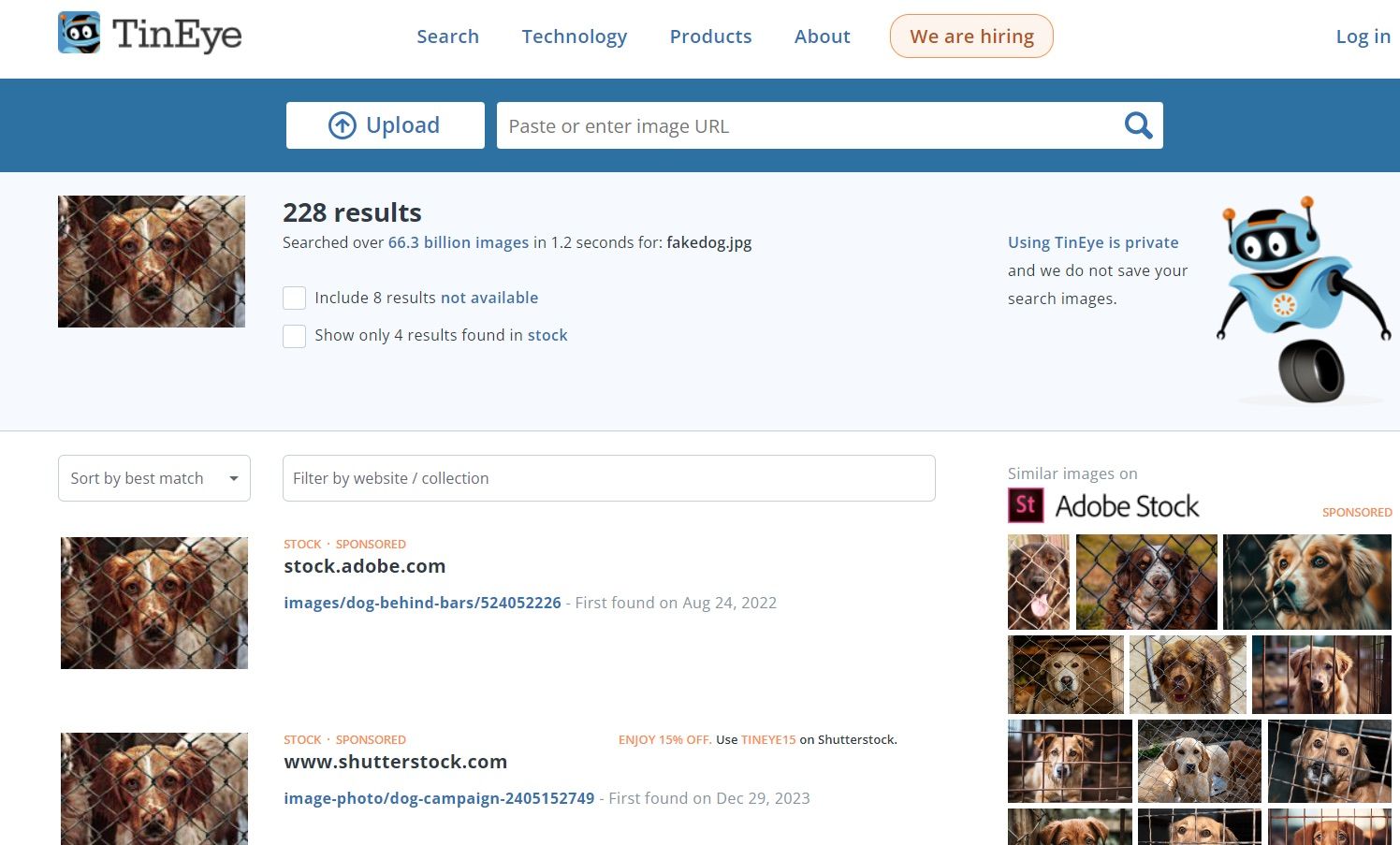
Canine from a shelter? No, from a photograph inventory
Photoshopped? We’ll quickly know.
Since photoshopping has been round for some time, mathematicians, engineers, and picture specialists have lengthy been engaged on methods to detect altered pictures mechanically. Some widespread strategies embrace picture metadata evaluation and error degree evaluation (ELA), which checks for JPEG compression artifacts to establish modified parts of a picture. Many widespread picture evaluation instruments, similar to Pretend Picture Detector, apply these strategies.
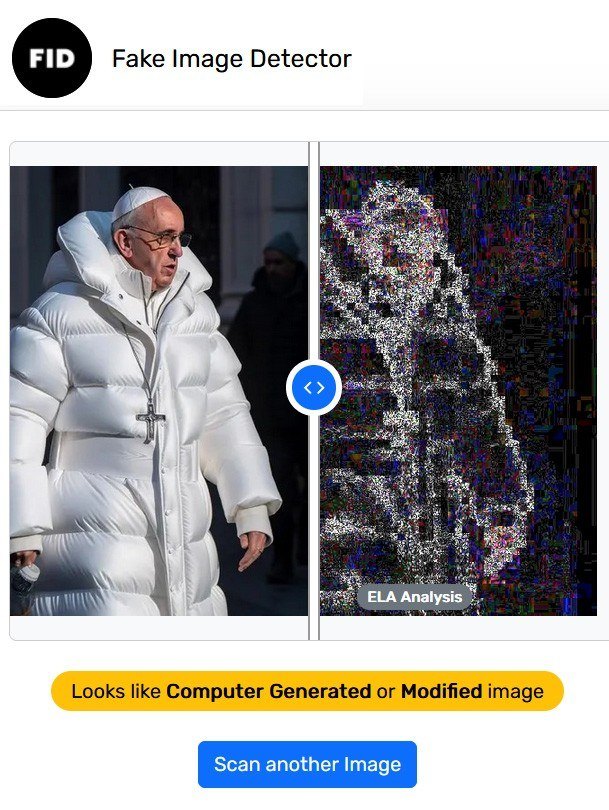
Pretend Picture Detector warns that the Pope most likely didn’t put on this on Easter Sunday… Or ever
With the emergence of generative AI, we’ve additionally seen new AI-based strategies for detecting generated content material, however none of them are excellent. Listed below are a number of the related developments: detection of face morphing; detection of AI-generated pictures and figuring out the AI mannequin used to generate them; and an open AI mannequin for a similar functions.
With all these approaches, the important thing drawback is that none provides you 100% certainty in regards to the provenance of the picture, ensures that the picture is freed from modifications, or makes it potential to confirm any such modifications.
WWW to the rescue: verifying content material provenance
Wouldn’t it’s nice if there have been a neater method for normal customers to verify if a picture is the actual deal? Think about clicking on an image and seeing one thing like: “John took this picture with an iPhone on March 20”, “Ann cropped the perimeters and elevated the brightness on March 22”, “Peter re-saved this picture with excessive compression on March 23”, or “No modifications had been made” — and all such knowledge can be unattainable to faux. Appears like a dream, proper? Properly, that’s precisely what the Coalition for Content material Provenance and Authenticity (C2PA) is aiming for. C2PA consists of some main gamers from the pc, pictures, and media industries: Canon, Nikon, Sony, Adobe, AWS, Microsoft, Google, Intel, BBC, Related Press, and a couple of hundred different members — principally all the businesses that would have been individually concerned in just about any step of a picture’s life from creation to publication on-line.
The C2PA customary developed by this coalition is already on the market and has even reached model 1.3, and now we’re beginning to see the items of the economic puzzle needed to make use of it fall into place. Nikon is planning to make C2PA-compatible cameras, and the BBC has already revealed its first articles with verified pictures.
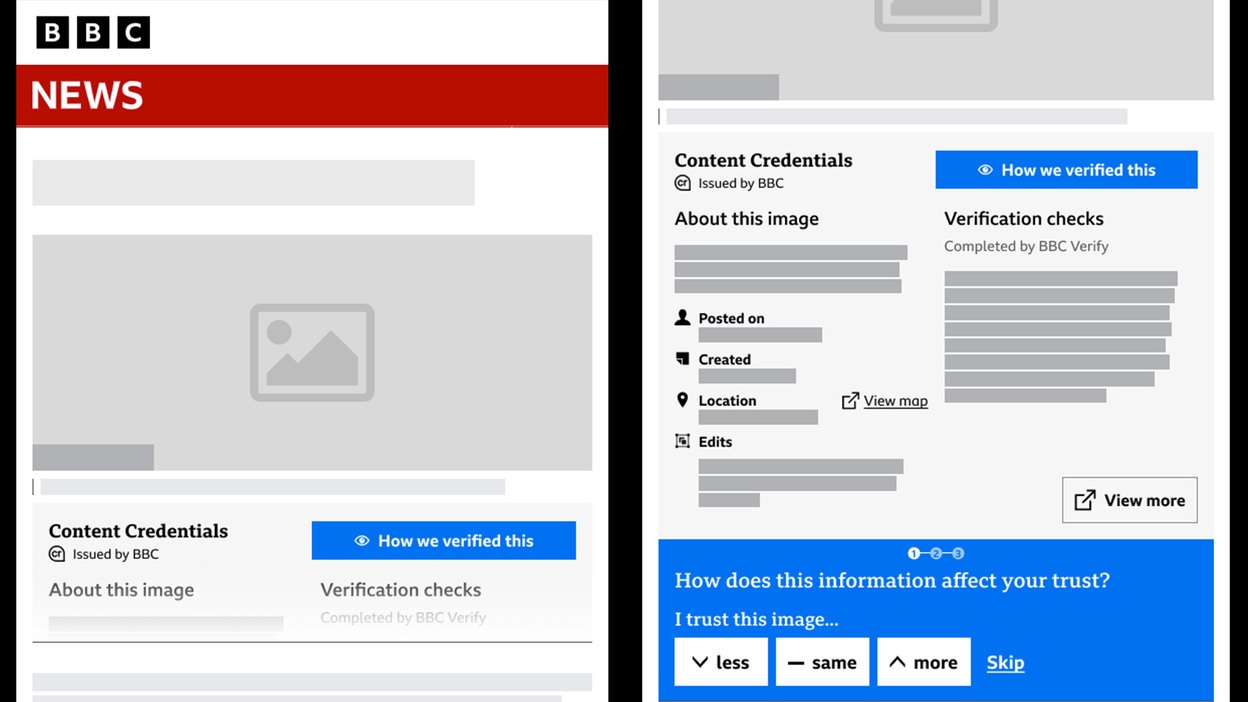
BBC talks about how pictures and movies in its articles are verified
The concept is that when accountable media retailers and large firms swap to publishing pictures in verified type, you’ll have the ability to verify the provenance of any picture straight within the browser. You’ll see slightly “verified picture” label, and once you click on on it, an even bigger window will pop up exhibiting you what pictures served because the supply, and what edits had been made at every stage earlier than the picture appeared within the browser and by whom and when. You’ll even have the ability to see all of the intermediate variations of the picture.
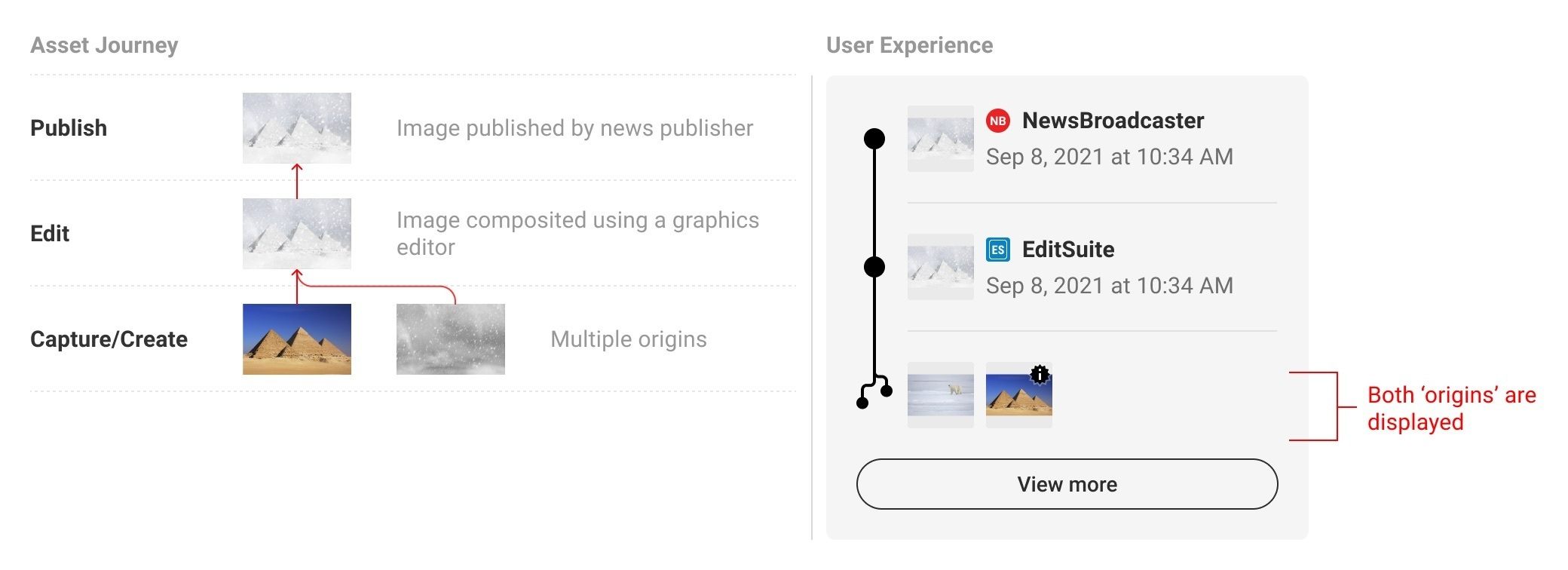
Historical past of picture creation and enhancing
This method isn’t only for cameras; it may well work for different methods of making pictures too. Providers like Dall-E and Midjourney may label their creations.
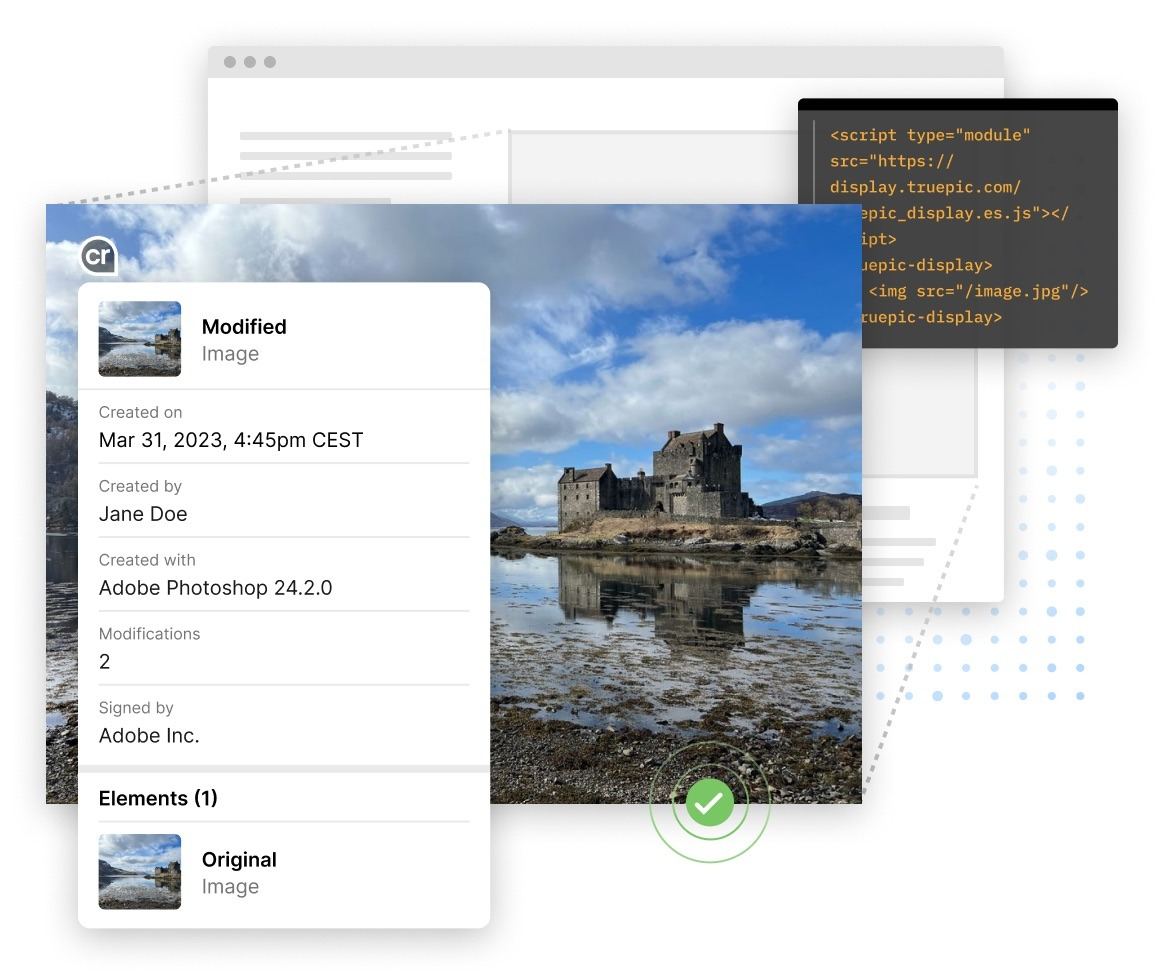
This was clearly created in Adobe Photoshop
The verification course of is predicated on public-key cryptography just like the safety utilized in internet server certificates for establishing a safe HTTPS connection. The concept is that each picture creator — be it Joe Bloggs with a specific kind of digicam, or Angela Smith with a Photoshop license — might want to receive an X.509 certificates from a trusted certificates authority. This certificates could be hardwired straight into the digicam on the manufacturing facility, whereas for software program merchandise it may be issued upon activation. When processing pictures with provenance monitoring, every new model of the file will comprise a considerable amount of additional info: the date, time, and site of the edits, thumbnails of the unique and edited variations, and so forth. All this will probably be digitally signed by the creator or editor of the picture. This fashion, a verified picture file can have a series of all its earlier variations, every signed by the one who edited it.
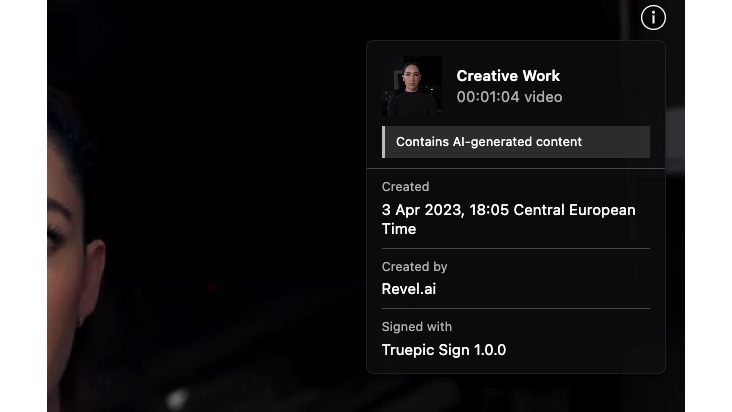
This video accommodates AI-generated content material
The authors of the specification had been additionally involved with privateness options. Generally, journalists can’t reveal their sources. For conditions like that, there’s a particular kind of edit referred to as “redaction”. This enables somebody to exchange a number of the details about the picture creator with zeros after which signal that change with their very own certificates.
To showcase the capabilities of C2PA, a group of check pictures and movies was created. You may try the Content material Credentials web site to see the credentials, creation historical past, and enhancing historical past of those pictures.

The Content material Credentials web site reveals the complete background of C2PA pictures
Pure limitations
Sadly, digital signatures for pictures received’t resolve the fakes drawback in a single day. In spite of everything, there are already billions of pictures on-line that haven’t been signed by anybody and aren’t going wherever. Nonetheless, as an increasing number of respected info sources swap to publishing solely signed pictures, any picture and not using a digital signature will begin to be seen with suspicion. Actual photographs and movies with timestamps and site knowledge will probably be virtually unattainable to cross off as one thing else, and AI-generated content material will probably be simpler to identify.

.jpg)

